MAC to IP Address Mapping
When managing networks, administrators often need to trace devices using various identifiers. While pinging to find IP addresses is common practice, sometimes you only have a MAC address to work with.
This scenario arises when investigating unknown devices on your network or troubleshooting connectivity issues. Understanding the relationship between MAC and IP addresses becomes essential in these situations.
IP addresses function as numerical labels that identify devices on networks. They serve dual purposes by identifying both the host interface and providing location information. These addresses must be unique within their specific address space, though private networks can reuse the same addresses independently.
IP addressing comes in two formats: the older IPv4 (like 192.168.1.1) using 32-bit addresses, and the newer IPv6 (such as 2001:0db8:85a3:0000:0000:8a2e:0370:7334) using 128-bit addresses to accommodate more devices.
In contrast, MAC addresses operate at a more fundamental level. These hardware identifiers consist of six hexadecimal pairs (example: 00:1A:2B:3C:4D:5E) and are permanently assigned by manufacturers to network interface cards. They function at the data link layer of the OSI model.
When devices communicate, the network interface card converts these hexadecimal MAC addresses into binary format for processing. While IP addresses identify network connections leading to devices, MAC addresses identify the actual hardware components handling those connections.
Public IP addresses have additional significance as they're globally unique and regulated by organizations like IANA and its regional authorities including AFRINIC, ARIN, APNIC, LACNIC, and RIPE NCC. This registration system allows for geographic tracing of connections, as specific address ranges are allocated to different regions worldwide.
Device identification in networked environments relies on layered addressing systems beyond IP alone.
Administrative command line tools provide access to critical network details like hardware and logical addresses.
Initiate the process by launching an elevated Command Prompt session through Windows search: right-click "cmd" results and enable administrator mode.
Protocols such as IPX/SPX demonstrate how MAC addresses historically functioned as primary identifiers before TCP/IP standardization.
Even with TCP/IP’s internet dominance, understanding cross-protocol addressing remains valuable for troubleshooting hybrid networks.
Hardware-bound MAC addresses persist as foundational identifiers across both legacy and modern network architectures.
In the Command Prompt, enter "ipconfig /all" to display a detailed configuration of your network interfaces. This command will provide you with an extensive list, including both IP addresses and MAC addresses associated with your network adapters.
When examining network interfaces, you can identify the MAC address, which appears as the physical address in network configuration details. In this particular instance, the MAC address is displayed as 70-71-bc-69-03-eb.
The system is assigned two different IP addresses based on different protocols:
- IPv4: 10.0.110.219
- IPv6: fe80::a034:180d:4963:369a%10
Linux users have multiple command options to retrieve IP address information through the terminal. Three particularly effective commands for this purpose are:
ip address
ifconfig -a
hostname -i
Each command provides slightly different information about your network configuration, allowing you to choose the most appropriate one for your specific needs.
Understanding how to locate an IP address based on a MAC address is a fundamental networking skill. When examining network commands, it's evident that different approaches yield varying levels of detail.
The "ip address" command stands out as particularly valuable for this task. This command provides comprehensive information about network interfaces and their associated addresses.
For advanced users, the command becomes even more powerful when combined with specific arguments. These parameters allow for targeted queries and filtering options that can be customized to your exact requirements.
To explore the full range of available options, accessing the help documentation is recommended. Simply append "--help" to view all possible parameters:
ip address --help
This documentation reveals numerous filtering capabilities that can streamline your search when working with multiple network interfaces or in complex networking environments.
With the right parameters, you can efficiently extract precisely the information needed to correlate MAC addresses with their corresponding IP addresses across your network infrastructure.
To locate an IP address using a MAC address, you can utilize the ip command with specific arguments. This command provides detailed information and allows for access control, configuration, and management of routes, neighboring devices, and network settings.
For macOS users, follow these steps to find the IP address:
- Click on the Apple logo in the top-left corner of your screen.
- Select System Preferences from the dropdown menu.
- Navigate to Network .
- In the Network window, select the connection type that is currently active (Wi-Fi or Ethernet). An active connection will be indicated by a green dot and the word Connected .
- The IP address will be displayed on the right side of the window, next to the selected connection.
Please note that the screenshot provided in the original content was taken from an emulator, which is why the IP address shown is 127.0.0.1, the default IPv4 loopback address. Your actual IP address will likely differ.
Finding a device's IP address through its MAC address can be a useful troubleshooting skill. When examining network information on your system, navigate to the detailed network settings panel.
Look for the section displaying connected devices, which is typically located in the lower right portion of the interface. Select the "Options" or "Advanced" button to reveal additional device information.
Within this expanded view, you'll find various network identifiers. The MAC address (Media Access Control) will be displayed among these details, usually formatted as six pairs of hexadecimal characters separated by colons or hyphens.
Once you have the MAC address, you can use network scanning tools or check your router's connected devices list to match the MAC address with its corresponding IP address. This method works across most operating systems with slight variations in the navigation path.
Finding your IP address through MAC address is possible using Terminal on macOS systems. For technical users comfortable with command-line interfaces, Terminal offers a straightforward approach.
To discover your local IP address, open Terminal from Applications > Utilities or by using Spotlight search. Once Terminal is open, simply type the command:
ipconfig getifaddr en0
This command specifically targets the en0 interface, which is typically your primary network connection on Mac devices. The system will immediately return your current local IP address.
For wireless connections, the en0 interface is usually appropriate, but if you're using Ethernet, you might need to use en1 instead. You can modify the command accordingly:
ipconfig getifaddr en1
This method provides a quick way to retrieve your IP information without navigating through system preferences or network settings menus.
For macOS users, terminal-based methods mirror Linux approaches
since both systems share Unix foundations
Windows administrators can utilize PowerShell cmdlets alongside traditional Command Prompt utilities
Third-party network scanning tools offer GUI alternatives across platforms
Router admin interfaces often provide device lists linking MAC and IP addresses
Remember that ARP cache queries remain a universal starting point
Cross-platform compatibility varies depending on network configuration specifics
Always verify results through multiple detection methods for accuracy confirmation
ARP and Network Discovery
Network analysis often requires cross-referencing hardware identifiers with logical addresses
Start by examining the ARP cache through terminal interfaces using system-specific commands
Windows, Linux, and macOS all support variations of the arp -v or arp -n syntax to display mappings
These tables reveal temporary bindings between MAC addresses and IPv4 addresses within your local subnet
ARP operates at the intersection of data link and network layers, dynamically updating device relationships
A Windows machine might display neighbors with interface-bound IPs, while Linux systems show complete cache entries
Physical and virtual network adapters maintain separate ARP tables, affecting visible results
For comprehensive discovery, consider scanning tools like nmap or checking router DHCP client lists
Wireless networks may require authentication before accessing complete address tables
Remember that ARP entries expire, typically within 300 seconds for most implementations
Finding an IP address using a MAC address involves utilizing the Address Resolution Protocol (ARP).
To understand the functionality of the ARP command, simply open your command prompt and type:
arp /?
This will display the help documentation that explains all available options and parameters for the ARP command.
The help feature provides comprehensive information about how to view your current ARP cache, add static entries, delete entries, and use various switches to customize your query results.
Understanding these options is essential when attempting to locate specific devices on your network based on their physical addresses.
Network administrators often need to reverse-engineer device connections by tracing IPs from hardware identifiers
Begin by accessing the Address Resolution Protocol (ARP) cache on your local machine
For Windows systems, open Command Prompt and type arp -a to display all cached MAC-IP pairings
On Linux terminals, use arp -n | grep [MAC] to filter results for a specific physical address
When local caches prove insufficient, network scanning tools like nmap become essential
Run nmap -sn [network-range] to perform a ping sweep
Cross-reference the output with arp-scan --localnet to map active devices
Enterprise environments benefit from checking DHCP server logs
Most DHCP systems maintain lease records showing assigned IPs and associated MAC addresses
Navigate to /var/log/dhcpd.log on Linux servers or check your router's web interface
For remote devices, leverage managed network equipment
Access switches/routers via SSH and execute:
show arp | include [MAC] (Cisco IOS)
display arp | include [MAC] (Huawei OS)
Third-party utilities like Angry IP Scanner automate the process
Configure custom columns to display both MAC addresses and corresponding IPs simultaneously
Advanced solutions like Wireshark capture real-time network traffic for forensic analysis
Always verify physical connections and VLAN configurations
Remember that wireless devices might show different MAC addresses depending on band (2.4GHz vs 5GHz)
MAC-IP relationships remain temporary and network-dependent
Network administrators often need to map hardware identifiers to network locations
when troubleshooting connectivity issues. One common approach involves correlating
MAC addresses with assigned IP addresses using built-in system tools.
Start by accessing your local network router’s administrative interface, which
typically lists connected devices with their MAC and IP pairings. For direct device queries,
the arp -a command in Terminal (macOS/Linux) or Command Prompt (Windows)
displays cached Address Resolution Protocol tables linking MACs to recent IPs.
Cross-platform tools like nmap or Angry IP Scanner can perform network sweeps
to identify active devices and their hardware addresses. For enterprise environments,
checking DHCP server logs often reveals historical MAC-to-IP assignments.
Remember that wireless networks and dynamic IP allocation may cause frequent changes,
so timeliness of data matters. Physical device labels or OS network settings menus
also provide MAC addresses for verification. Always ensure proper authorization
before probing networks to maintain compliance and privacy standards.
Network visibility is limited for regular users - you can only view MAC addresses of devices within your own subnet using the ARP command.
This limitation doesn't apply to network administrators, who have comprehensive visibility across the entire network infrastructure.
For administrators managing Windows environments, Active Directory provides powerful capabilities for tracking devices. The DHCP list within Active Directory contains complete records of all network devices, storing their MAC addresses as unique identifiers alongside their corresponding IP addresses.
This centralized management approach enables administrators to maintain a complete inventory of all connected devices regardless of subnet boundaries.
Manual IP and MAC address tracking via CLI or enterprise systems poses challenges for many organizations
Repetitive command-line processes become impractical in large networks with frequent connectivity issues
Continuous monitoring for unauthorized devices isn’t feasible without automation or scripting expertise
High-cost enterprise solutions like Microsoft AD often exceed budget constraints for smaller businesses
FREE network scanners emerge as optimal solutions, offering automation and cost efficiency
These tools eliminate manual intervention while providing critical network insights
Key evaluation metrics for effective IP-MAC resolution tools include:
- Cross-referencing of IP assignments with device MAC addresses
- Identification of static vs. dynamic IP allocations
- Detection mechanisms for duplicate IP assignments
- DNS hostname resolution capabilities
- Multi-platform compatibility
- Availability of free versions with functional value
Four cost-effective solutions stand out:
Eusing Free IP Scanner delivers rapid Windows-based scanning with MAC address mapping for specified IP ranges
ManageEngine OpUtils Free Edition offers scaled-down enterprise features, supporting both Windows Server and Linux environments
Paessler PRTG provides essential IP scanning functions in its free tier, optimized for Windows Server deployments
Spiceworks IP Scanner excels in heterogeneous networks through cloud-based agents compatible with Windows, Linux, and macOS
For organizations managing mixed-OS infrastructures, Spiceworks’ solution offers distinct advantages
Its lightweight agent technology enables non-intrusive scanning without network performance degradation
The cloud-based architecture facilitates seamless integration with free IT asset management systems
Automated network monitoring tools not only resolve address conflicts but also provide foundational data for comprehensive network management
These free alternatives prove particularly valuable for budget-conscious teams requiring continuous oversight capabilities
Spiceworks IP Scanner streamlines network oversight by offering cloud-based device discovery and management capabilities accessible from any location.
Unlike traditional monitoring systems, this solution integrates with lightweight agents deployed across Windows, Linux, or macOS environments to map network assets dynamically.
The platform generates real-time inventories detailing device specifications, connectivity status, and security postures through automated polling mechanisms.
Administrators gain visibility into outdated operating systems, unpatched vulnerabilities, and exposed network ports - critical data for maintaining infrastructure security.
Cloud architecture enables centralized monitoring of distributed networks while integrating with complementary IT management modules like help desk systems.
Though lacking offline functionality, its web-based interface simplifies tracking service availability and port configurations through color-coded status indicators.
Key functionalities include:
- Cross-platform agent deployment for persistent network surveillance
- Automated detection of unauthorized open ports
- Patch compliance reporting for proactive risk mitigation
- Historical device connectivity tracking through timestamped logs
Primarily adopted by small-to-medium enterprises, the tool provides enterprise-grade monitoring without subscription costs.
Windows-centric administrators particularly benefit from its portable executable format (433KB) enabling rapid deployment and immediate network audits.
Free registration unlocks continuous asset tracking alongside Spiceworks' ecosystem of IT management utilities.
This solution bridges the gap between basic network scanners and comprehensive monitoring suites through scalable, browser-accessible diagnostics.
Network Scanning Tools Overview
A versatile network scanning tool offers immediate insights into the status of connected devices. It presents a comprehensive list of all active devices on the network, including their IP addresses, MAC addresses, user names, and open ports.
Users can opt to scan a specific section of the network or focus on a single IP address to check its usage. The flexibility extends to scanning non-sequential IP addresses, which can be imported from a text file.
Key Features:
- Scans a specified range or the entire network
- Displays all system addresses
- Utilizes a multi-threaded architecture for fast results
- Allows exporting of results
This tool, known as a free IP scanner, is adept at mapping IP addresses to MAC addresses by scanning the network. It also provides an option to run a port status scan on each detected device. The IP scanner delivers on-demand services for local networks.
Thanks to its multi-threaded architecture, scans are completed quickly. Results can be viewed directly in the utility or exported to a CSV file for further analysis in a spreadsheet or other tools.
The simplicity and ease of use of this IP scanner make it a valuable asset for network administrators. It is particularly useful for troubleshooting and routine checks to ensure all devices remain accessible. The tool can function as a visual ping or help identify a specific device.
Additional Benefits:
- A lightweight application, suitable for older machines
- Provides straightforward information on address ranges, hostnames, ports, and users
- Allows users to define and limit their scanning range
- Ideal for short-term tests, not recommended for long-term monitoring
Download the free version of this IP scanner to start managing your network more efficiently.
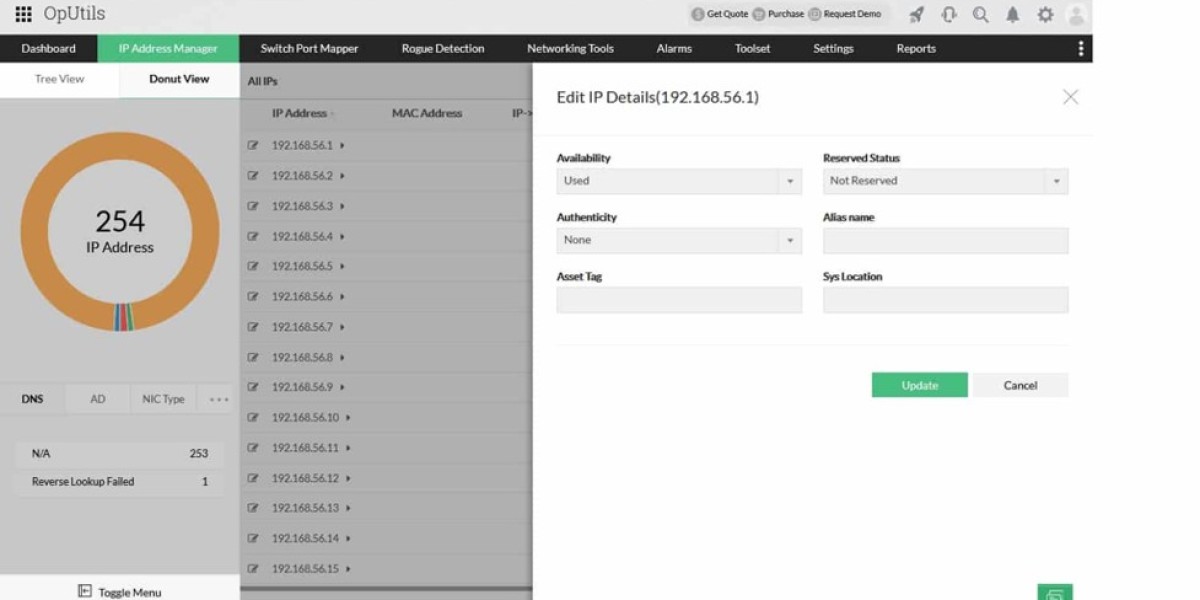
Another notable tool is ManageEngine’s OpUtils , developed by Zoho, a company renowned for its online office and business software. OpUtils continues this tradition of high-quality, performance-driven software.
OpUtils: A Comprehensive Network Management Solution
OpUtils serves as a powerful network monitoring and switch port mapping tool, available for deployment on Windows Server or Linux environments. For cloud-based operations, a paid version can be integrated with AWS accounts. New users can explore the full capabilities through a 30-day trial, while the free edition provides access to 16 essential utilities including an IP scanner.
Notable capabilities include:
• Comprehensive mapping between IP and MAC addresses
• Flexible network scanning options (complete network or specific address ranges)
• Device manufacturer identification
The ManageEngine OpUtils specialist package delivers complete address tracking functionality across IP addresses, MAC addresses, port numbers, and switch ports. It enables administrators to view IP-MAC address relationships while providing DNS and DHCP server verification to identify unauthorized network connections. The system clearly distinguishes between dynamically and statically assigned addresses.
Even the free version includes diagnostic tools like ping and traceroute for network troubleshooting. This solution empowers administrators to resolve between MAC and IP addresses while maintaining comprehensive network control, making it particularly valuable for business environments and larger network infrastructures.
ManageEngine offers an extensive collection of IT monitoring solutions. Typically, organizations begin with OpManager (their primary network monitoring platform) before adding OpUtils as a complementary tool.
Key advantages include:
• Combined IP management and physical switch port monitoring
• Integrated troubleshooting capabilities
• Cisco and SNMP compatibility for configuration, administration, and diagnostics
• Enterprise-focused functionality
• Advanced features beyond home network requirements
For those seeking alternatives, Paessler PRTG provides a flexible monitoring solution with a free tier supporting up to 100 monitors. PRTG automatically discovers network devices, generates topology maps, and displays comprehensive addressing information including IP addresses, MAC addresses, and hostnames.
Discovering Device Identities: Linking MAC and IP Addresses
Network administrators often need to correlate MAC addresses with IP addresses to properly manage their networks. This relationship forms the foundation of local network communications and can provide valuable insights for troubleshooting and security purposes.
Understanding the Connection
MAC (Media Access Control) addresses are permanent hardware identifiers assigned to network interfaces, while IP addresses serve as logical identifiers within a network. The Address Resolution Protocol (ARP) bridges these two addressing systems, maintaining tables that map MAC addresses to their corresponding IP addresses.
Tools for Address Resolution
Several options exist for finding IP addresses using MAC addresses:
Command Line Utilities
The ARP command (arp -a) quickly displays all cached MAC-to-IP mappings on your local network. This built-in tool works across operating systems but only shows currently active devices.
Network Monitoring Solutions
For enterprise environments, comprehensive solutions like Paessler PRTG offer advanced capabilities:
• Automated network discovery
• Device inventory management
• Performance monitoring with alerts
• Traffic analysis with NetFlow/sFlow support
• Hostname and manufacturer identification
The free version supports up to 100 sensors, making it suitable for small businesses. The full solution requires Windows Server for on-premises deployment, with cloud options available.
Security Implications
MAC address information has important security considerations:
• MAC addresses cannot traverse beyond your local network
• Unknown MAC addresses in your ARP table may indicate unauthorized devices
• Your MAC address is visible to your router and can potentially be used to track activity
• VPNs can help protect privacy by masking your actual MAC address
Finding Your Own MAC Address
On Windows systems:
Navigate to Start → Settings → Network & Internet → Status → View hardware and connection properties
Look for "Physical address (MAC)" in the displayed information.
Understanding these relationships helps maintain network integrity and can assist in identifying potential security concerns in your connected environment.
What is a Netflix VPN and How to Get One
A Netflix VPN is a specialized tool designed to bypass geographic restrictions, enabling viewers to unlock diverse libraries of shows and movies not available in their local region. By masking the user’s IP address and rerouting traffic through servers in other countries, a Netflix VPN grants access to global content while maintaining privacy. This service is ideal for streaming enthusiasts seeking broader entertainment options or added security during online viewing.
Why Choose SafeShell as Your Netflix VPN?
If your Netflix VPN is not working due to outdated software or detection issues, SafeShell VPN offers a seamless solution with unmatched benefits:
- High-Speed Netflix-Optimized Servers
SafeShell’s specialized servers deliver ultra-fast connections for buffer-free streaming, ensuring 4K-quality playback without disruptions.
- Multi-Device Compatibility
Connect up to five devices simultaneously, including Apple TV, Android TV, and smartphones, for flexible access to Netflix across your household.
- Exclusive Multi-Region App Mode
Unlock content from various Netflix libraries at once, letting you switch between regions effortlessly to discover global shows and movies.
- Zero Speed Throttling
Enjoy unlimited bandwidth and lightning-fast speeds for downloads and streaming, eliminating lag even during peak hours.
- Advanced Security with ShellGuard
Military-grade encryption and anti-leak protocols protect your data, ensuring anonymous browsing and secure access to geo-blocked content.
- Risk-Free Trial Experience
Test SafeShell’s premium features—from HD streaming to multi-device support—with a flexible free trial, no payment required.
By addressing common issues like Netflix vpn not working , SafeShell combines cutting-edge technology and privacy-focused tools to redefine your streaming experience.
A Step-by-Step Guide to Watch Netflix with SafeShell VPN
Unlocking global Netflix content has never been easier with SafeShell Netflix VPN . Here's how to get started:
- First, sign up for a SafeShell VPN subscription by visiting their official website and choosing a plan that suits your needs
- Download the SafeShell app for your specific device, whether it's Windows, macOS, iOS, or Android
- After installation, open the app and log into your account
- For optimal Netflix streaming, select APP mode when prompted
- Browse through the server list and choose a location that offers the Netflix content you want to watch (popular options include US, UK, and Canada)
- Connect to your selected server with just a single click
- Once connected, open Netflix either through the app or website and log in as usual
- Now you can enjoy unlimited access to region-specific Netflix shows and movies without any restrictions